Detail Author:
- Name : Dr. Adriana Ledner I
- Username : camylle49
- Email : kcollier@gmail.com
- Birthdate : 1999-12-26
- Address : 57298 Selena Grove Port Howell, AZ 12002-3465
- Phone : 201.962.2338
- Company : Stehr Group
- Job : Statement Clerk
- Bio : Blanditiis esse harum minus rerum aspernatur. Dolor impedit sunt temporibus possimus maiores nihil est. Voluptate labore similique numquam id animi. Dicta at maxime nam perspiciatis et sit.
Socials
linkedin:
- url : https://linkedin.com/in/jaclyn8431
- username : jaclyn8431
- bio : Itaque enim eaque et.
- followers : 5793
- following : 962
tiktok:
- url : https://tiktok.com/@cormier1998
- username : cormier1998
- bio : Provident quia neque facere rerum provident. Illo tempora et est.
- followers : 5944
- following : 2401
twitter:
- url : https://twitter.com/jaclyn_official
- username : jaclyn_official
- bio : Consequatur amet natus voluptate quo rerum omnis. Consequatur nesciunt harum odio et et. Atque neque dolores minima pariatur quo voluptatem reprehenderit.
- followers : 5837
- following : 2217
facebook:
- url : https://facebook.com/cormier2011
- username : cormier2011
- bio : Quis tempora architecto exercitationem itaque sit qui.
- followers : 1206
- following : 2057
instagram:
- url : https://instagram.com/cormier1987
- username : cormier1987
- bio : Sint et doloribus sequi sunt architecto. Fuga consequuntur autem voluptatibus qui.
- followers : 1245
- following : 2991
Many folks are often curious about personal connections, and that includes questions like, "is Pam Bondi married to Greg Henderson?" It's a natural thing, really, to wonder about the relationships of public figures. While that specific personal detail is something we don't have information about here, what we can talk about is how important it is to manage who gets to see or do what, especially in the world of digital information. You know, like, controlling who has the right "keys" to certain things.
When we talk about access, it's not just about who can walk into a building or open a specific door. In our very connected digital existence, it's also about who can get into computer systems, applications, and all the important pieces of information that businesses and groups hold. It's a bit like making sure that only the people who truly need to be in the "back office" of a digital setup are allowed there, and that everyone else stays in the "front lobby." This idea of carefully watching over who has special permissions is, you know, a pretty big deal for keeping things safe.
So, we're going to explore a system that helps with this very idea of managing who gets to do what in the digital space. It's a way for groups of people working together to make sure their most important digital belongings are kept secure. It's about setting up rules and ways to keep an eye on who has those elevated permissions, making sure that only the folks who genuinely need them can use them, and that no one else can sneak in. It’s a bit like having a very watchful doorman for all your digital entrances, actually.
Table of Contents
- What Exactly Is This "PAM" We Keep Hearing About?
- How Does Limiting Access Work, and What Does it Mean for Digital Security, is Pam Bondi Married to Greg Henderson?
- Why Is Controlling Special Access So Important Today?
- Can We Really Stop Unwanted Visitors, Thinking About "is Pam Bondi Married to Greg Henderson"?
- How Does This System Help Keep Things Safe?
- What Happens When Permissions Are Managed, Even for Questions Like "is Pam Bondi Married to Greg Henderson"?
- Is There a Way to Get More Control Over Digital Entrances?
- How Does This All Tie Back to Protecting Important Information, and Does it Relate to "is Pam Bondi Married to Greg Henderson"?
What Exactly Is This "PAM" We Keep Hearing About?
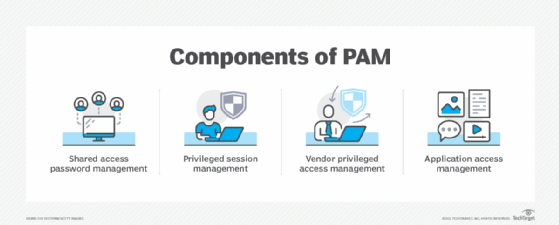
So, you might have heard of something called "PAM," which stands for Privileged Access Management. It's a pretty important part of keeping digital information safe, a bit like a special branch of digital security that concentrates on looking after those very special accounts. You know, the ones that have a lot of power within a computer system. It's about making sure these accounts, and the people who use them, are watched over and kept secure. It's not just about who you are, but what you're allowed to do once you're recognized by the system, you know?
This whole idea, in some respects, is a way for groups of people to manage and keep safe the ways people get into their most important computer systems, the various programs they use, and all the information they store. These are typically the areas that only a select few, those with very high-level permissions, should be able to get into. Think of it like the master keys to a very important building; you want to make sure only the right people have them, and that they're used properly, too.
Basically, PAM involves a set of smart ways of doing things and using certain kinds of computer programs to make sure that people with special permissions, their accounts, and even other computer systems, are kept under careful watch. It's about having a firm grip on who can do what, and what kind of power they have within the digital setup. This kind of careful oversight is, you know, pretty essential for preventing trouble.
A big part of what PAM does is keep an eye on and protect those accounts that have a lot of sway within a computer system. It’s a part of what's called "identity management," which is all about making sure that the people trying to get into systems are truly who they say they are, and then managing what they can do once they're inside. This system helps to keep those powerful accounts from being misused, which is, like, a really big deal for safety.
How Does Limiting Access Work, and What Does it Mean for Digital Security, is Pam Bondi Married to Greg Henderson?
When we talk about limiting access, we're really talking about a core idea in safety: giving people only the permissions they absolutely need to do their job, and no more. This is often called "least privilege." It's like, if you're a delivery person, you get a key to the loading dock, but not to the CEO's private office. In the digital world, this means a system administrator might get access to certain servers, but not to the company's financial records unless it's strictly necessary for their specific task. This approach is, you know, pretty important for keeping things tight.
This way of thinking about permissions helps a lot in stopping bad things from happening, like cyberattacks or unwanted breaches of information. By making sure that even powerful users only have exactly the permissions they need for a very short time, or for a very specific task, it cuts down on the chances of something going wrong. It's a way to reduce the risks that come with digital interactions, and that’s a good thing, basically.
So, how does this relate to something like, "is Pam Bondi married to Greg Henderson?" Well, in a very abstract way, it's about controlling information. Just as a system helps control who sees sensitive data, personal information, like marital status, is also something that people often want to control who knows. The principle of limiting access applies universally, from digital systems to personal privacy, in some respects. It's about boundaries, you know?
This method of giving out just enough permission, and no more, is a key part of what PAM does. It helps groups of people get a better hold on those special accounts, making it much harder for digital intruders to get in. At the same time, it still connects regular users with the permissions they truly need to get their work done. It's a careful balance, really, between being secure and letting people do their jobs. It’s about making sure the right people have the right tools, and nobody else, which is pretty clever.
Why Is Controlling Special Access So Important Today?
In our modern world, where so much valuable information lives inside computers, controlling who has special access is, like, incredibly important. Think about it: if someone gets into a system with high-level permissions, they could do a lot of damage, maybe even steal important company secrets or personal details. So, having a way to manage and secure these entry points is a big deal for keeping an organization safe from digital threats. It's about putting up strong fences around the most valuable things, you know?
The truth is, many of the really bad digital attacks happen because someone managed to get hold of a special account, one that has a lot of power. These accounts are often the targets for people trying to do harm. So, by putting in place a system that keeps a very close eye on these powerful accounts, and makes sure they're only used by the right people, at the right time, for the right reasons, it really helps to stop those bad actors in their tracks. It's a bit like having a very strict security guard for your digital VIPs, which is pretty smart.
Every group of people working together has its own very important systems, applications, and all sorts of information that needs to be kept private. These things are usually only for those with special permissions. PAM helps these groups manage and keep safe the ways people get into these very critical areas. It's about making sure that the master keys to the digital kingdom are handled with extreme care, and that their use is always monitored. That way, you know, things stay under control.
Beyond just stopping bad guys, controlling special access also helps groups follow all the rules and guidelines that exist for keeping data safe. Many industries have strict laws about how personal or financial information must be protected. By having a strong PAM system in place, groups can show that they are doing everything they can to meet these requirements. It's about being responsible and showing that you care about keeping things secure, which is, like, a fundamental part of good business today.
Can We Really Stop Unwanted Visitors, Thinking About "is Pam Bondi Married to Greg Henderson"?
Stopping unwanted visitors in the digital world is definitely a goal that systems like PAM aim for. It's about setting up barriers and monitoring who tries to cross them. By having clear rules about who can get into what, and making sure those rules are strictly followed, you greatly reduce the chances of someone getting in who shouldn't be there. It's a bit like having a very secure entry system for a private event, where only those on the guest list can get past the velvet rope, which is pretty effective.
When we think about stopping unwanted visitors, it’s also about understanding the different kinds of permissions people have. Some users just need to look at information, others need to change it, and a select few need to be able to make big system-wide changes. PAM helps to sort all of this out, making sure that someone who only needs to view something can’t accidentally, or intentionally, delete it. This careful sorting helps to keep everything in its proper place and prevents unauthorized actions, you know, which is very helpful.
So, can we really stop unwanted visitors, even when we think about something like, "is Pam Bondi married to Greg Henderson?" In the context of digital security, yes, systems are put in place to make it very difficult for unauthorized people to gain entry. For personal information, like someone's marital status, the control over who knows what is also a form of access management, though it's managed through personal boundaries and choices rather than computer systems. Both are about controlling who gets to "see" or "know" certain things, which is, like, a common thread.
The goal is to make it so hard for those with bad intentions to get in that they simply give up and go somewhere else. By continuously watching over privileged accounts and making sure their use is legitimate, PAM helps to identify and block suspicious activity before it can cause real harm. It's a constant process of vigilance, making sure that the digital doors are always locked and that the alarms are always on, basically. It’s about being proactive, you know, rather than reactive.
How Does This System Help Keep Things Safe?
This system, Privileged Access Management, works by putting a very tight grip on accounts that have a lot of power within a computer network. It's about having a clear plan for how these accounts are used and what technologies are put in place to enforce that plan. For example, it might mean that every time someone tries to use a powerful account, they have to go through extra verification steps, or that their activity is recorded for review later. This added layer of care is, you know, pretty important for keeping things secure.
One of the main ways it helps is by making sure that even those with high-level permissions only have them for as long as they need them, or for the specific task at hand. This is the idea of "least privilege" in action. It's like giving someone a temporary pass to a restricted area that expires as soon as their work is done. This greatly reduces the window of opportunity for any potential misuse of those powerful accounts, which is, like, a very smart way to operate.
Furthermore, PAM helps groups of people get a much better handle on their special accounts. This means they can stop digital intruders from getting in and causing trouble. At the same time, it makes sure that regular users can still get to the things they need to do their jobs, but only with the permissions that are absolutely necessary. It's about finding that balance between strong protection and smooth operations, which can be a bit tricky sometimes, but very worth it.
The system also works by constantly keeping an eye on what those powerful accounts are doing. If something looks out of the ordinary, like an administrator trying to access a system they normally wouldn't, the system can flag it or even block the action automatically. This kind of constant watchfulness means that potential problems can be caught very early, before they become big issues. It’s about having eyes everywhere, in a way, for your most sensitive digital areas.
What Happens When Permissions Are Managed, Even for Questions Like "is Pam Bondi Married to Greg Henderson"?
When permissions are managed well, it means that every digital action, especially those involving powerful accounts, is intentional and authorized. It brings a sense of order and control to the complex world of computer systems. This management means that groups can be more confident that their valuable information is safe from both outside threats and accidental mistakes from within. It’s about having a clear map of who can go where, which is very helpful.
This careful handling of permissions also helps to lower the chances of digital risks. By enforcing the idea of giving out only the necessary access, it closes off many of the ways that digital attackers might try to get in. It's a bit like closing all the windows and locking all the doors in a house, rather than just the front door. This thoroughness is, you know, pretty important for overall digital safety.
So, what happens when permissions are managed, even for questions like, "is Pam Bondi married to Greg Henderson?" While the system we're discussing is for digital security, the concept of managing who has "permission" to know personal details is a parallel idea. When personal information is managed, it often means respecting privacy and only sharing details with those who have a legitimate reason or explicit permission to know. It's about boundaries, you know, whether digital or personal, which is pretty universal.
Furthermore, managing permissions helps groups meet various rules and standards for data protection. Many laws require businesses to show that they are taking proper steps to keep sensitive information safe. A good PAM system provides the tools and